-
Step Ten – It’s all About the Journey (Keeping the Strategy Relevant)
This blog walks cybersecurity professionals through the logical steps to create a practical and actionable cybersecurity strategy.
Always make sure to keep your cybersecurity strategy up to date and adjust it when required.
You may recall during my concluding paragraph in Step Zero, where I discussed the Basics of Cybersecurity Strategy, I emphasized that a Cybersecurity Strategy is a living thing.
The strategy should never be assumed to be set in stone – fixed and unchanging. A good strategy is dynamic and open to evolution as circumstances change or new opportunities present themselves. But it never loses its purpose or ability to guide to motivate the organization to move forward in a meaningful way.
Set a cadence to regularly review the strategy as it is being operationalized. Twice a year is a reasonable timeframe. Be aware however that there may arise circumstances – good and bad – that will require you to re-think some aspects of your strategy and incorporate this new information into your plans.
When working to review your strategy, here are a couple of things to consider.
Look for the Good as well as the Bad
There is an adage that applies to any significant events that will impact your strategy: “Never let a good crisis go to waste”.
Be aware of changes in the environment – locally, regionally, globally – that may predicate a need to revisit and revise the strategy to fit with the new reality. It’s not all bad though – a new technology may have been released that will drastically improve your cybersecurity operational capabilities. Or a nation state’s cybersecurity attacks have been radically curtailed sue to a regime change.
In any event, be on the look out for changes that will have a measurable impact on how you do cybersecurity. A few examples may be, but not limited to, the following areas:
- New attack vectors that affect your organization
- Evidence of new threat actors targeting your industry with specific intent
- A global event that changes how the organization operates (e.g., the COVID pandemic)
- A change in the organization’s fundamental goals or direction
- A new product, offering or service the organization has developed that will be certainly a target for competitors and/or nation states and eCrime organizations
Some events may be so significant or impactful or happen so quickly that you would be advised to act on revising your strategy immediately instead of waiting for the next review cycle.
Side Note:
Some people might say, “If this new change or event is so significant, I won’t have time to plan ahead, I’ll be purely in reaction mode dealing with the situation.” There is no denying the importance of dealing with a crisis – either good or bad – as quickly as possible. But, that doesn’t mean your strategy should be set aside. You may recall in my Introduction, I compared the difference between reactive and proactive cybersecurity administration with Smoke Jumping and Fire Management. Both have a very important part to play. And while the professionals are putting out the fires, the leadership needs to also be planning how to manage that forest for the future so that what caused this fire is analyzed, understood and incorporated into any plans moving forward. Your strategy must be revised to accommodate the new event and make sure you are prepared to be proactive about it in the future.
The Road is Never Always Straight
Over the course of operationalizing your cybersecurity strategy via the Roadmap (discussed in Step 9), you will likely find things don’t always go as planned. That shouldn’t be a big surprise. Some projects may go longer than planned, the budget may be cut, a particular strategic objective may not be as relevant as it was the year before. For whatever the reason, it will be important to shift and adapt the strategy as circumstances warrant over the course of its realization. This doesn’t lessen the work put into developing the strategy or mean the strategy is somehow a failure. Far from it. This is merely the normal – and expected – evolution of the strategy to account for the real world. Remember this:
A good cybersecurity strategy will grow and evolve without losing its power to be your North Star.
Conclusion
That wraps up my 10 steps in the pragmatic guidance on developing and operationalizing a Cybersecurity Strategy for your organization. Moving forward, I will be addressing other aspects of cybersecurity strategic planning, including thoughts on the supply chain and the importance of aligning with cybersecurity frameworks.
I hope you have found this blog useful so far. I look forward to publishing further blogs in the future and hope to hear from you as you work on your own cybersecurity strategy
Thank you for your time. Be sure to stay tuned for the next posting in this series: Cybersecurity Strategy – The Chain is Only as Strong (Incorporating 3rd Party Suppliers).
-
Step Nine – How Do We Get There? (Defining the Operational Roadmap for the Strategy)
This blog walks cybersecurity professionals through the logical steps to create a practical and actionable cybersecurity strategy.
You must clearly outline what actions you are going to take, and over what time period, to make your Cybersecurity Strategy real.
The success of your strategy rests totally on its practical operationalization. Not only must you be able to clearly articulate what actions you will take to accomplish the strategy (i.e., your Objectives and Key Results – See “Step Seven – But What Will It Do?”), you must outline the tasks, projects, initiatives and programs in a digestible timeline – your Roadmap. And that Roadmap must include what it will take to get there (e.g., costs, resources, time, etc.)
When working to define and build your Roadmap, here are a few things to consider.
Start with the Objectives as Your Guide
You may recall we discussed setting up your Objectives and Key Results in “Step Seven – But What Will It Do?”. This should easily provide you your blueprint for the roadmap. One of the primary recommendations to follow from Step Seven was to lay out the Key Results in a way that would accomplish the Objectives. Remember, each Key Result should outline a required task, project, initiative or program. So, the next step is to lay out the order in which these activities will be implemented (i.e., your timeline). Each Objective should have its own set of activities laid out in a logical timeline that tells the story of how that Objective will be accomplished.
The key benefit of laying out your Roadmap timeline aligned with your Objectives is that it provides a tangible picture of how and over what time each Objective of your Cybersecurity Strategy will be realized.
It’s in the Details
Laying out a logical timeline of activities is only one part of the Roadmap; there are a lot of other things to define that will go toward making the Roadmap more practical and valuable. The roadmap must be looked to as a north star for the operationalization of the cybersecurity strategy. As such, there are a lot of details that must be incorporated to give it optimal value. These include the following:
- Duration of the Key Activities – This should go without saying but it is imperative to estimate the projected duration of each of the tasks, projects, initiatives and programs. At this stage, it doesn’t have to be down to the last second; this is a reasonable projected estimate for budgeting purposes. For example, have three ranges for the activities (e.g., less that three months, between three and six months, or greater than six months, or whatever works for your environment).
- Complexity and Resource Requirements – Is the particular task, project, initiative or program a quick job that can be done by a single person or is it a monolithic affair requiring a team of experts for months on end? Something in between? Again, keep in mind that this is a reasonable projection. You can estimate complexity in terms of what you anticipate it will take technically and operationally (e.g., Low, Medium, and High) and how many resources you estimate it will take to get it done (e.g., less than 3 resources, between 3 and 10 resources or more that 10 resources or whatever works for your environment).
Side Note:
When discussing the matter of technical and operational “Complexity” for a proposed action, there are a number of possible contributing factors. From the technical standpoint for example, is this a simple re-configuration of an existing solution, or does the action entail the deployment of an entirely new security system for example. Does the proposed action include a lot of moving parts? From an operational standpoint, does the proposed action merely require your existing team members to execute using existing processes and procedures? Or does the action entail the re-envisioning of your operational model? Or even a re-organization of a department (e.g., a consolidation of teams, formation of a new team) for example?
- Costs – This projection would take the previous factors into account to estimate – at a very high level – what it will cost to get the job done. Again, don’t go down to nickels and dimes; use ranges (e.g., less that $100K, between $100K and $500K or greater than $500K or whatever works for your environment).
- Metrics – When we discussed Objectives and Key Results in Step Seven, we mentioned the importance of ensuring the Key Results (i.e., the tasks, projects, initiatives and programs in your Roadmap) were measurable. Determining measurements for your Key Results were premature at that stage. The Key Results are now translated to tangible activities and it is here that we must work them out. Metrics are a key element to determining success and it is important to keep in mind that the determination of effective metrics require a great deal of collaborative discussion and agreement on what success looks like (e.g., “100% of privileged human identities are identified and under full governance.”, “Migrate all 3rd-party developers to a secure virtual desktop environment within 6 months.”, “Enroll at least 80% of laptops in MDM by the end of the calendar year.”, etc.). Therefore, this is something that should be done with other colleagues, key decision makers and stakeholders.
When outlined properly, your Roadmap will provide a rich set of details for stakeholders to understand what it will take to operationalize your Cybersecurity Strategy and what benefits it will provide the organization.
But there are two additional very important items to consider.
Priorities and Risk Statements
Regardless of how awesome the Roadmap ends up looking or how compelling a story it tells, you have to be realistic about the fact that not all of the proposed activities may be approved. So, it is critical to do two things to allow for a more clear choice of what parts of the Roadmap should be considered above others:
Prioritization – It is important to place a priority on each task, project, initiative or program in the Roadmap. This may typically be within their Objective “family”. Similarly, it is important to prioritize the Objectives so that, if the entire Roadmap is not economically feasible or viable, you can trim the Roadmap by Objective, rather than by individual actions.
Risk Statements – As important as it is to outline the benefits the component tasks, projects, initiatives or programs within a Roadmap will have, it is perhaps equally important to articulate the risk of any of these not being executed. Each activity in the Roadmap should have a well thought-out Risk Statement outlining what the organization is risking by not going through with it. It is preferable to make the Risk Statement objective (i.e., in terms of cost to the organization) if possible. However, a subjective risk statement is better than none at all.
Be Realistic
When developing your Roadmap and its component activities, be conscious of the practicality of the timeline and how long it takes to deliver results. Be realistic about what you can get done – either with your own resources or with the help contractors. And, even if you had adequate resources, be realistic about the amount of change the organization can – or is willing to – absorb. Technical and operational changes can be jarring if they’re too radical or done too quickly.
Also, when estimating such things as complexity and cost, don’t be afraid to get outside perspectives and advice. Remember that you’re not in this alone. And that is a good segue to …
It Takes a Village
Just as with almost every other aspect of the Cybersecurity Strategy, many hands make light work. Be sure to bring in other experts from within or outside of the organization to aid in the development of the Roadmap. Lean on Key Decision Makers and Stakeholders when looking for that reality check on the Roadmap’s details. As always, whenever you involve others in the process, their engagement and buy-in will be all the greater.
Thank you for your time. Be sure to stay tuned for the next posting in this series: Cybersecurity Strategy Step Ten – It’s All About the Journey (Keeping the Strategy Relevant).
Special thanks to Karel Beukes for his very valuable contributions to this post.
-
Step Eight – How Do We Know When It’s Working? (Defining Metrics)
This blog walks cybersecurity professionals through the logical steps to create a practical and actionable cybersecurity strategy.
You must be able to measure the successful realization of your strategy as it is operationalized.
You will recall I said earlier that the cybersecurity strategy should be considered a living thing that should be reviewed and revisited on a continual basis to ensure it is 1) still relevant and 2) doing what you want it to. To help accomplish #2, you need to establish realistic and tangible metrics that can tell you how well your strategy is being executed – your vision realized.
But what kind of metrics would be appropriate for measuring the successful operationalization of a cybersecurity strategy? Let’s think about that. When working to define your metrics, here are a few things to consider.
Don’t Confuse the Strategy’s Metrics with Your OKR Metrics
There is a fundamental difference when you are considering what metrics will allow you to understand how well your strategy is being realized as opposed to the initiatives and projects being executed to accomplish the strategy. It is this:
Cybersecurity Strategy Metrics allow you to determine how well and/or effectively the vision and objectives of the strategy are being realized over the lifetime of the strategy.
Objective and Key Results (OKR) Metrics (measurements) will allow you to determine how well or effectively your individual projects, initiatives and programs are being delivered and whether they are achieving the stated requirements. This is oriented on a project-by-project basis and is basically tactical.
Focus Metrics on Measuring the Successful Realization of the Vision and Goals of the Strategy
When determining your metrics, be sure to focus on the long-term objectives of the strategy and what it is trying to achieve for the organization. They have to address the high-level requirements the organization needs cybersecurity to accomplish and do so in a manner that is easy to understand by non-technical audiences.
Here are a few examples.
- If the organization has, as one of its strategic objectives, the need to improve its ability to maintain their operational capabilities, it can develop the following metric:
Enterprise Resilience – Enhance business continuity and disaster recovery preparedness capabilities. Measure the effectiveness of these programs with respect to their ability to allow operations to continue and recover in the face of incidents and/or disasters.
- If the organization has, as one of its strategic objectives, the need to improve compliance with policies and greater consistency in operations, it can develop the following metric:
Policy and Standard Exceptions – The number of exceptions and exception extensions against current policies and standards will be measured to determine formal compliance with published organizational requirements. The expectation is that, as the organization moves to align its administrative and operational activities with established policies and standards, the number of exceptions and extensions should lower on a continual basis.
- If the organization has, as one of its strategic objectives, the need to improve user involvement in securing the organization’s information ecosystem, it can develop the following metric:
User Engagement – The organization will measure the effectiveness of efforts to raise user awareness of cybersecurity best practices and their collaboration and partnership in both securing the organization’s assets and safeguarding customers’ privacy. This effort will also work to establish their general level of engagement with information security through such metrics as, self-reporting of issues, surveys on security events and phishing response rates.
Other metrics might include, depending on the organization’s priorities:
- Reduction of Risk
- Improved Threat Telemetry Gathering and Analysis
- Service Coverage
- Vulnerability Management Improvement
- Application Security Metrics
- Network Defence Metrics
- Delivery Against the Strategic Plan Roadmap
You will notice that the above examples do not outline specific measurements; only that they are to be determined. This is intentional as the strategy is pointing out what must be measured and why. How it is to be measured may be a considerable effort and would likely require the collaborative input of a number of resources. There may be technical and operational requirements in monitoring and scaling the metrics. Therefore, metrics are to be determined during the execution of the strategy and the how does not necessarily belong in the plan document.
The main message here is to focus on those metrics that clearly communicate whether the cybersecurity strategy is succeeding in accomplishing vision; the big picture. Ultimately, make sure they are clearly defined, can be tangibly monitored and empirically measured.
Finally, as with many parts of a cybersecurity strategy, stand ready to adjust the metrics as the need arises. The measurements may need to change as the strategy evolves or changes and should not necessarily be set in stone. As the strategy moves forward, make sure the metrics you have put in place are providing useful intel or whether they need to be:
- Augmented;
- Adjusted; or
- Retired.
Thank you for your time. Be sure to stay tuned for the next posting in this series: Cybersecurity Strategy Step Nine – How Do We Get There? (Defining the Operational Roadmap for the Strategy).
-
Step Seven – But What Will It Do? (Determining the Objectives and Key Results)
This blog walks cybersecurity professionals through the logical steps to create a practical and actionable cybersecurity strategy.
Your cybersecurity strategy must clearly articulate how you will address your Risk Statements and realize your Future State and Vision.
This is where the rubber hits the road. What, specifically are you seeking to accomplish with your strategy and what tasks must be accomplished to get there? This stage will provide the logical outline of tasks, initiatives and projects that will eventually go into you Roadmap (more on that in Step Nine).
At this point, you must state your Objectives and the Key Results (OKRs) associated with operationalizing your strategy. You first have to define your Objectives and, once you have done that, then the Key Results required to accomplish each[1].
But how do you articulate the objectives? You should have everything you need from the prior steps. Consider the following diagram:
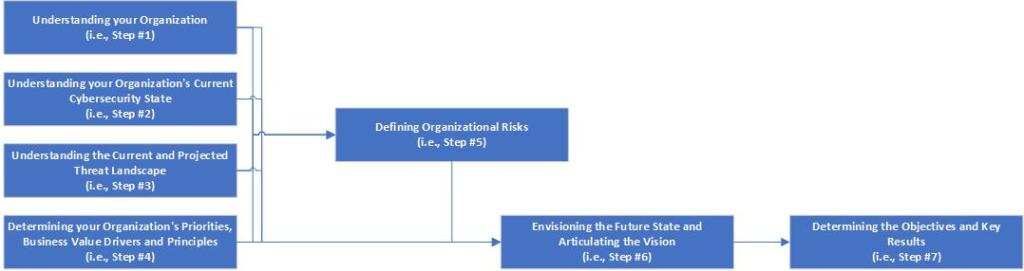
The Cybersecurity Strategy Development Flow To get here, you have:
- Worked to understand the organization’s Purpose, Priorities, its current Cybersecurity Capabilities, and the Threats it is likely to face (i.e., Steps 1-4).
- Used that information to define the Risks to the Organization (i.e., Steps 5).
- Used all of the information and analysis from the prior five steps to envision a Future State and accordingly define a Vision Statement (i.e., Step 6).
So now:
- Your Objective(s) should logically flow from the prior steps to determine on what major areas you will need to focus.
I won’t get into what the objectives should be as there will be too much variability. But I will say this:
The objective should frame an accomplishment that can be directly attributed to a critical element of the future state.
Side Note:
If, for example, the envisioned Future State depends in great part on the modernization of the organization’s Identity and Access Management (IAM) framework, and the current scope of IAM is limited or has coverage gaps, one possible Objective statement could be: Identity governance is established across all human and non-human digital identities across all hosting models.
Once you have defined your Objectives, you can then consider what specific series of tasks must be delivered in order to accomplish them (i.e., the Key Results).
When working to define your OKRs, here are a few things to consider.
The Objectives Must Connect Back to Risks, Business Priorities and Future State
The whole point of this exercise is so that you can – with facts and evidence – demonstrate to the organization’s key decision makers that the Objectives of the strategy are solidly grounded in the organization’s own priorities, goals and objectives. Having followed the steps outlined in the graphic above, you can easily provide the background data that supports how your objectives will directly address the business’s needs. By doing so, you are also by the way, demonstrating how the envisioned Future State is also addressing those needs.
Side Note:
In order to ensure the operationalization of the Strategy is feasible, it is recommended to try to restrict the number of Objectives to no more than five. Creating more may make the realization of the strategy unrealistic, prohibitively expensive and/or complex. If you feel this is too small a number, use your best judgement. In this case, prioritize the Objectives and, for those un-realized Objectives, create a Risk Register (i.e., as mentioned in “Cybersecurity Strategy Step Two: Where Are You?”)
Key Results Must Together Achieve the Objective
The Key Results for an Objective should be thought of those activities that, when delivered, will accomplish the stated Objective. They should together comprise the sum total of all activities that will be required.
Depending on their complexity, the Key results can be framed in the form of tasks, initiatives, projects, or full programs. Many of these may already have been developed in some form or other during the establishment of the organization’s current Cybersecurity State (i.e., “Cybersecurity Strategy Step Two: Where Are You?”).
The Key Result should be framed as a tactical activity that can achieve a specific goal. For example, you could draft the folowing Key Result:
“Modernize Privileged Access: Leverage Security technologies to modernize and enforce Privileged Access policies and procedures.”
You must keep it specific however and not try to generalize across multiple areas of focus (e.g., keeping Threat Detection separate from Incident Response).
Side Note:
To help ensure the execution and delivery of the Key Results, it is recommended to try to restrict the number derived to no more than five per Objective. As above with Objectives, too many Key Results may make the delivery unwieldly and overly complicated. Remember however, that some Key Results – if complex enough – may be defined in terms of a long-term program of sub-projects. This assumes a lengthy delivery and the involvement of a number of dedicated resources focused on this one area. In those cases, phrase the Key Result to encompass all that the program would deliver.
Key Results Must Be Measurable
One crucial element of the Key Results, however, is that their delivery must be measurable in some way. This is already true of most projects and programs, so should come as little surprise[2]. The Key Result must have some measurement to indicate whether it was successful in it’s aim (e.g., “100% of privileged human identities are identified and under full governance.”, “Migrate all 3rd-party developers to a secure virtual desktop environment within 6 months.”, “Enrol at least 80% of laptops in MDM by the end of the calendar year.”, etc.). The scope is very important here.
Side Note:
Determining measurements for your Key Results may be premature at this stage. It requires a great deal of collaborative discussion and agreement on what success looks like. At this stage, focus your efforts on defining the Objectives and the Key Results that will accomplish them. Defining the scope and measurement of success for a Key Result may best be done during the creation and drafting of the Cybersecurity Strategy’s Operational Roadmap (i.e., “Cybersecurity Strategy Step Nine: How Do We Get There?”)
Finally, Key Results measurements should not necessarily be set in stone. Like most projects and programs, it is a good practice to regularly review the measurements to make sure they still make sense and whether they need to change or evolve as they work progresses.
Thank you for your time. Be sure to stay tuned for the next posting in this series: Cybersecurity Strategy Step Eight – How Do We Know When It’s Working? (Defining Metrics).
[1] In Agile terminology, you can think of the Objectives as Epics and the Key Results as the Features (i.e., components that contribute to the Epic).
[2] In Agile terminology, you can think of the Measurable aspects of the Key Results as the User Story (i.e., user value story that contributes to the Feature).
-
Step Six – Dare to Dream (Envisioning the Future State and Articulating the Vision)
This blog walks cybersecurity professionals through the logical steps to create a practical and actionable cybersecurity strategy.
Clearly communicate your ideal future state to show your aspirational vision for cybersecurity.
At this point, you can build on everything you have gathered and built to define your target state. Now that you have done the leg work to understand what the organization is about, where it’s going, the current state of your cybersecurity function and the risks your organization faces, you are now in a position to figure out where you want to take the cybersecurity function – to define the target/future state. While it must be practical, it must also inspire and demonstrate your aspirations.
The key word here is “aspire”. It is vitally important to be able to imagine and communicate what you envision as your ideal future state in order to generate enthusiasm and anticipation to move forward. This is a key element to getting key decision makers and stakeholders to buy into your vision. It demonstrates having a footing in reality while also keeping an eye open for the art of the possible.
Imagine, for example, the following:
- Bad actors are detected in seconds…
- The workforce can securely share information any time, anywhere…
- A new user can get exactly the privileges they need for their role in minutes…
- Identities cannot be stolen…
- Passwords do not exist…
- Data is automatically classified and protected…
- Users can click fearlessly.
Aspirational statements can motivate and generate positive dialogue regarding your Vision. The first step is to develop a list of your aspirations for the future state – what you want to be able to accomplish in the long-term (i.e., the next 3-5 years). This may be considered you ideal future state so don’t hesitate to go all out. What would you like to achieve in a perfect world? Go there! You’re developing a Vision after all. You can worry about coming back down to earth in the later stages.
Once you have worked out a solid depiction of your aspirational future state, you are ready to boil it down into your Vision Statement.
The Vision
Defining the future state for your audience must start with your Vision Statement. The Vision will be stated in one sentence to provide a clear north star for the strategy to move toward. Everything else afterward will be developed with the sole intention of achieving the Vision. Therefore, the Vision must encapsulate what the future state will accomplish for the organization (i.e., your aspirations) in a way that is:
- Forward looking;
- Inspirational; and
- Practical
With that in mind, here are a couple of things to consider.
Make the Vision Relatable
While it is important that the Vision be forward-looking, do not lose sight of the fact that it must depict a future state that maps to your organization’s goals and objectives. That’s the whole point after all.
When drafting the Vision Statement, be aware of everything you have learned up to this point and what the organization needs from the cybersecurity function to be able to accomplish its own vision. There must be synergy!
Side Note:
One organization was in the midst of a massive transformation to a more service-oriented as opposed to a product-oriented enterprise. The cybersecurity function had to show itself to be cognizant of this move. The statement had to ensure that the vision articulated a way forward, outlining a journey that allowed the organization to securely realize that transformation in a manner that managed risk and prepared them for this new model. This had to be a foundational element.
While a Vision Statement may need to be grounded in the organization’s goals however, it must still be inspirational.
Generate Excitement
It bears repeating that the Vision Statement must be encouraging, motivating, and exciting! It needs to drive the members of the cybersecurity function in realizing the vision. And of equal importance is the need to ensure the stakeholders and the key decision makers can get behind the vision and approve the budget to see it become a reality. No pressure.
Side Note:
Using the above example, the need was to combine what the organization planned to accomplish (i.e., transforming to a service-based enterprise) with a message that allows people to get behind the Vision. After a great deal of thought, the Vision Statement was published as:
Evolve into a world class cybersecurity organization, with governance and processes that reduce risk to acceptable levels, enabling Contoso to move to the next level and securely deliver services for its customers and partners
You may read the Vision Statement and think to yourself that it sounds somewhat generic. Don’t worry; that’s the nature of them. They have to be forward looking while also allowing for a great deal of flexibility and adaptiveness. A Vision Statement is not about specifics, it’s about the far horizon, which is broad.
In the end, the Vision Statement, and the Future State it depicts, has to be simple and act as a North Star. Don’t go into excessive detail. That’s not what the Vision Statement is about. Keep it short and sweet.
Finally, it needs to be said that the envisioned future state is an outline of the things you seek to accomplish at a high level. It will not entail technical detail or a security architecture. It is not intended to. Detail and architecture are just a couple of parts of the realization of the strategy and should not be part of the strategy at this point. There are a few more things to do before going there.
Thank you for your time. Be sure to stay tuned for the next posting in this series: Cybersecurity Strategy Step Seven – But What Will It Do? (Determining the Objectives and Key Results).
Special thanks to Karel Beukes for their contributions to this post.
-
Step Five – What’s The Worst That Can Happen? (Defining Organizational Risks)
This blog walks cybersecurity professionals through the logical steps to create a practical and actionable cybersecurity strategy.
Your cybersecurity strategy must clearly articulate the risks the organization faces and the possible consequences.
We’re at a pivotal part of the development process for creating a winning cybersecurity strategy! We have by now collected the foundational information and intelligence required to determine what shape the strategy must take. To recap, we have:
- Collected the data relevant to what you organization is all about: Who Are You?
- Determined the current state of your organization’s cybersecurity capabilities: Where Are You?
- Researched the current and projected threats and trends relevant to your organization: Who Goes There?
- Established the organization’s primary goals, objectives, and drivers: What’s in It for Me?
This is the point where we amalgamate this gathered data and intelligence to analyze it. The intent is to determine and define the risks facing the organization that we must primarily be concerned with. Everything collected up to this point should be enough to allow you to form a clear picture of the risks facing your organization.
Side Note:
At this point, don’t be too focused on what you’re going to do about those risks. You first want to state them. The statement itself, however, will usually provide you with a pretty clear picture of what you need to subsequently do.
A few people may say:
“What’s the point of outlining the risks? Isn’t that already clear from the gaps outlined in the current state assessment and from the threat research?”
There may be some folks with that position. But they have to remember two key points:
- Cybersecurity is, ultimately, about managing risk. It’s not enough to understand the gaps and possible threats we face now and in the future. It’s the risks these elements present to the organization. And those two aren’t the only sources of risk; they’re just very important components.
- Somebody has to pay for the Cybersecurity Strategy. Will key decision makers care enough about gaps in the current cybersecurity posture and some potential threats enough to approve a pricey budget to deal with them? Remember we need to make sure we are connecting what we have learned to what is important to the key decision makers and, by extension, the rest of the organization.
Side Note:
It goes without saying that any risks you outline here are with the full understanding of what the organization’s Enterprise Risk Management (ERM) function is already looking at. They are typically a key decision maker in most scenarios anyway. However, as we all know, ERM’s focus is broader than cybersecurity. So, our intent here is to focus on those organizational risks that have a connection with cybersecurity.
With that in mind, here are a couple of things to think about:
Remember Who’s Risks They Are
When you are working out the risks to the organization, articulate the risks in a manner that demonstrates their impact to the organization, not to cybersecurity. You’re not addressing cybersecurity risks when you’re presenting to the key decision makers, you’re addressing their risks.
Side Note:
How we address those risks (more on that in a later blog post) will of course be articulated from the cybersecurity perspective. But there must be a clear connection between the risks facing the organization (and the key decision makers in particular) and the subsequent actions cybersecurity will take as a result.
When determining the organizational risks, you will have to make sure you are drawing on everything you learned in the first four steps, bring them all together and frame them from the business perspective as opposed to a cybersecurity perspective. Here is an – admittedly high-level – example:
- From “Who Are You?”, you have determined the following: The organization is a state agency that has a mandate to provide effective services to the citizenry in as short a time as possible. The agency’s priority for the next two years is to launch an automated service utilizing new Cloud technologies to reduce the amount of time citizens have to wait to receive a response and receive their requested service.
- From “Where Are You?”, you have determined the following: An assessment of the organization’s current cybersecurity state reveals that the information security function has a security architecture that is purely on-premises focused and they have no capabilities to secure a Cloud-based environment (or associated applications) at this time.
- From “Who Goes There?”, you have determined the following: An analysis of current and projected threats indicates that there are numerous current threat vectors that would target this type of service and could potentially compromise the application and its data (with potentially sensitive information such as Personally Identifiable Information – PII) with ease.
- From “What’s in It For Me?”, you have determined the following: Key decision makers have stated that the launching of this service is an imperative and will be key to improving the agency’s reputation as it is currently seen as behind the time and notoriously slow to adapt.
From this intelligence, we can define the following sample risk description/consequence:
Risk: Inability to support and secure Digital Business Transformation Initiatives
Description: The current information security function lacks the capability to support our organization’s digital transformation goals. Without the ability to secure the planned digital workload and environment, there is a high risk of compromise and data loss or theft. This would result in serious reputational damage to the agency and exposure to potential legal action. Failure to move forward with the digital transformation initiatives however will present to the public the perception that we are not modernizing or adapting with the times.
In this manner, you can determine and state risks to the organization that will allow the key decision makers and stakeholders to establish a connection with what is important to them and what you are trying to address – for the organization.
Don’t Go Behind the Curtain
Finally, it needs to be established that you should not determine the risks in isolation. It’s important to retain your hold on the concept of open communications and collaboration during the definition of organizational risks. You are working to formulate the risks in a manner that articulates the risks to the business in a language that connects the key decision makers to them. It’s therefore important to maintain that connection and present the risks as you define them to the key decision makers and stakeholders for their feedback and impressions. Much like with business drivers, goals, and objectives, having their input and involving them in this process will only increase their buy-in and sense of ownership over the resulting cybersecurity strategy.
Thank you for your time. Be sure to stay tuned for the next posting in this series: Cybersecurity Strategy Step Six – Dare to Dream (Envisioning the Future State and Articulating the Vision).
Special thanks to Karel Beukes for their contributions to this post.
-
Step Four – What’s In It For Me? (Determining your Organization’s Priorities, Business Value Drivers, and Principles)
This blog walks cybersecurity professionals through the logical steps to create a practical and actionable cybersecurity strategy.
Your cybersecurity strategy must reflect a clear understanding of the organization’s priorities, goals, and drivers.
You may recall during the introduction to this blog series I stated that one of the secrets to drafting a winning strategy was to know your audience. Not to put too fine a point on it, but:
Your audience will be those parties who will determine whether your strategy is worth the organization’s time and money to implement.
So, when drafting your cybersecurity strategy, you must make sure it resonates with the key decision makers (and those people to whom the decision makers either answer to or whose opinion matters). Their concerns are not typically around cybersecurity. Their concerns will be broader and/or unique to their own role. You must find a way to connect with what’s important to them and ensure the cybersecurity strategy reflects that connection.
I mentioned two important tenets in a previous post: “Step Zero – Cybersecurity Strategy Isn’t Something to Be Scared Of”:
- Cybersecurity Strategy is about bringing value and looking forward
- Cybersecurity Strategy is helping the organization securely get to where it’s going
In a nutshell, this is what the key decision makers need to see from your cybersecurity strategy. The strategy needs to be seen as an enabler for the organization that will bring tangible value and allow the organization to achieve its goals in a way that keeps risk to a manageable level. To do that, the strategy must first articulate the priorities, goals and drivers that are of the highest importance to the key decision makers.
But how do you find out, specifically, what’s important to the key decision makers? We’ll assume you’ve already followed the recommendations from “Step One – Who Are You?” and have a good idea of what the organization’s about and from where it creates and derives value. The next step is straightforward: Talk to the Key Decision Makers.
Getting it Straight from the Top
The best way to understand what the leadership team deems important is to get it directly from them. Typically, the best way to do that is to do the following:
- Identify the Key Decision Makers: Target those key decision makers that are primarily responsible for the direction of the organization and the development of its goals and priorities. Note: Be sure to keep in mind that the cybersecurity strategy will affect certain decision makers more than others (e.g., the COO, CIO, Chief Risk Officer, etc.). If there is a long list of stakeholders, focus your efforts on those decision makers that are 1) chiefly responsible for approving your strategy and providing budget, and 2) more likely to be affected by the information technology ecosystem and the cybersecurity function. Very often, they will be one and the same.
- Prepare the Questions: While any conversation with the decision makers is best framed as free flow and conversational in nature, prepare a set script of questions that you need answered. You may also have questions stemming from your research on the organization as a whole (i.e., from Step 1 – Who Are You?). For example, what is the key decision maker’s role in operationalizing the organization’s overall strategic plan. Make sure that whatever questions you ask eventually get around to what you need to know for your cybersecurity strategy. The questions should never be yes or no style. They should allow for thought and consideration. Include something along the lines of the following:
- What are your key responsibilities?
- What are your priorities in the mid- to long-term (e.g., 1-3 years)?
- What are your primary goals and objectives in the mid- to long-term (e.g., 1-3 years)?
- What are the primary risks you see in achieving your goals and objectives?
- What are your top pain points and challenges; the things that keep you up at night?
Side Note:
If you find the decision maker being interviewed thinks the questions are too broad, you can narrow down the scope of their questions to focus more on the information technology ecosystem and cybersecurity. However, you want to make sure they are able to express to you what is important to them.
- Schedule one-on-one interviews/meetings: One-on-one meetings face-to-face are always best, if possible, but take what you can get. It is important to make sure the meeting allows you to make a connection (if one doesn’t already exist) and establishes a relaxed environment. Also, it is likely you will be limited in terms of the decision maker’s available time so try to keep the meeting to 45 or 60 minutes. That should be enough to give you what you need.
Side Note:
Keep the conversation moving and try to get as many of the questions answered as possible – without making the decision maker feel they’re being rushed (or interrogated).
- Take Notes and Get Validation: It may go without saying, but be sure to document everything you discuss. Structure the notes so that you can send them back to the decision maker for their review and feedback. This will ensure:
- There was no misunderstanding or miscommunication.
- The decision maker knows they were heard.
- The decision maker is afforded the chance to make any necessary clarifications or additions.
- Analyze Your Findings: Compile the information gathered to find the Key Takeaways from each interview. Look at the data singly and in aggregate to gather what you determine are the Primary Considerations from the decision makers. This, coupled with what you understand about the organization, will allow you to articulate – in the decision makers’ own words – the organization’s Priorities, its Business Value Drivers, and its Key Objectives.
Following this framework will produce several benefits. Not only will it allow you to get the information you need, but you will have done it in a way that brought the key decision makers into the process. This collaborative approach will aid in building their trust that the strategy is going to focus on those areas that are of greatest relevance to them and the organization. Also, reflecting their priorities in your strategy will help to increase their sense of ownership and partnership in the resulting document.
The interview-based approach outlined above highlights two very important concepts that need to be embraced when developing a winning cybersecurity strategy:
From Blocker to Enabler
How often has the Information Security function been seen by the rest of the organization as the “Department of No”? As the Blocker? Now, this is not entirely the fault of the Information Security management and staff. There’s plenty of blame to go around (especially when a department wants to place a new workstream into production with zero input from Information Security).
Often, this negative perception is fundamentally due to the lack of information sharing, effective communications and collaboration across departments and divisions within the organization.
If we want that to change, we must be the catalyst.
By demonstrating a desire to include people from outside Information Security to help craft the strategy, you are exemplifying the open communications mindset and leading by example. You are showing yourself to be an enabler for the organization, rather than a blocker.
Executed properly, this should provide the impetus for other parts of the organization to embrace security as a partner. It may not be immediate, but the example presented by Information Security – the Department of No – would set an excellent precedent.
Open Communications – Reaching Across the Silos
In many organizations the information ecosystem is segmented into any number of pillars with their own hierarchies and priorities. Communications is rarely directly across but rather goes to the top, moves across and then down. In some other scenarios, the Information Security function may be responsible for securing the digital ecosystem, but a lot of the operational pillars of cybersecurity may be outside of their direct control. For example, one organization had a mandate to mature its cybersecurity capabilities across the board, but such functions as Identity and Access Management, Business Continuity and Patch Management were outside of their managerial control.
In these situations, it is impossible to develop a realistic and actionable cybersecurity strategy without opening the doors and involving these key decision makers and stakeholders to be a part of the cybersecurity strategy development process. Developing a cybersecurity strategy by including key decision makers and organizational stakeholders is a fantastic way to reflect a genuine belief in open communications and collaboration. If they are asked to participate and contribute to crafting the Priorities, Business Value Drivers, and Key Objectives on which the strategy will be determined, then your chances of getting them to support the execution of the strategy will get exponentially better.
The Principled Approach
While some may think this optional, I think the subject an organization’s principles worthy of mentioning here.
Principles are fundamentally guides to behaviour. Most organizations have formally published a list of principles to help define their culture and how their employees are expected to conduct themselves as representatives of the organization. Principles are carefully thought out and reflect what the organization is about and what it stands for. As such, it is important to be cognizant of your organization’s formal principles – if it has them – and make sure they are not only called out, but that you articulate how the strategy will ensure it aligns with and adhere to those principles. This one act can go a long way toward attaining buy-in from a broad representation of the organization as it reflects your effort to make the cybersecurity strategy a part of the organization at a foundational level.
Thank you for your time. Be sure to stay tuned for the next posting in this series: Cybersecurity Strategy Step Five – What’s the Worst that Could Happen? (Defining Organizational Risks).
Special thanks to Michael Howard and Karel Beukes for their contributions to this post.
-
Step Three – Who Goes There? (Understanding the Current and Projected Threat Landscape)
This blog walks cybersecurity professionals through the logical steps to create a practical and actionable cybersecurity strategy.
“Forewarned, forearmed; to be prepared is half the victory.”
Miguel de CervantesAs you work to develop a cybersecurity strategy and to improve your organization’s capabilities, always be sure to look down the road to what threats you can expect to experience in the near- and long-term.
When looking to determine the threats your organization is likely to face, it goes without saying you should be looking both at the broad picture as well as what you can expect to see from threat actors based on your industry or geography.
Side Note:
Analyzing adversary Tactics, Techniques, and Procedures (TTPs) is a key type of threat trend that organizations should focus on in terms of evaluating (or re-evaluating) their cybersecurity architecture, operations and, ultimately, their cybersecurity strategy.
Regardless of whether you’re in the public sector or private sector, whether you are in health, retail, banking or located in the U.S. or France or Japan (or multiple locations), you need to remember one cardinal rule about threats:
It may sometimes be about nation states, but it’s certainly always going to be about the money.
It is very rare – outside of direct military conflicts – that cyber attacks will be for purely malicious reasons. With few exceptions (e.g., a nation state looking to disrupt a rival state’s critical infrastructure) the vast bulk of threats boil down to e-crime and making money. Even nation states are looking to leverage their attacks to “profit” by it on one way or another (e.g., espionage, upsetting the operation of government, stealing IP to use for their own industries, etc.).
You’ll remember when I posted Step 1 (Who Are You?), I asserted it was critical to understand your organization and what distinguished it from others – where it derives its value. That is fundamental to accurately identifying what projected threats and threat trends you need to be aware of – both globally and specific to you. Which threats would have the biggest impact to your organization, in terms of value lost? What threats would cause you to lose the most value fastest? When researching projected threat trends, always keep in mind what your organization values most and what assets it must protect above all others. This will help to focus on and prioritize those threats that can directly impact your most highly valued assets.
Side Note:
Bad actors have shifted their efforts in recent years from malware attacks to harvesting user credentials, typically through phishing attacks. This includes targeted attacks on the C-Suite. Anticipating this trend has allowed numerous organizations to devise strategies around more robust Identity and Access Management and enhanced protection around privileged (e.g., executive, administrative, etc.) credentials.
Industry- and Region-Specific Threats
A great deal of available research provides insights into threats that target specific industries and regions in addition to those that are global and indiscriminate. For example, industries such as mining, manufacturing and utilities will be very concerned about preparing for threats to their Operations Technology (OT) infrastructure, as much or more so than their Information Technology (IT) infrastructure and would accordingly direct focus on those. In addition to industry, it is important to be aware of any threats that are specific to the region or country in which you’re located.
Many industries have a dedicated Information Sharing and Analysis Center (ISAC) for cybersecurity awareness and coordination to ensure that members of that industry are informed of and preparing for threats that are of particular importance. Please refer to the Industry-Specific Sources Section below for some examples.
Side Note:
Verizon regularly publishes its Data Breach Investigations Report (DBIR) and provides insights into the degree to which regions around the world have been attacked as well as the nature and motives/objective(s) of these attacks. This report also calls out attack patterns by industry to provide an outline of the degree to which various industries were attacked and the nature of those attacks. This is one example. Please refer to the Suggested Resources section below for more ideas for research sources.
In addition to independent reports, most governments provide services and threat reports to aid and support efforts by local organizations to strengthen and protect their information ecosystems. This is a valuable resource to leverage when conducting threat and threat trend research. Please refer to the National Sources Section below for some examples.
Side Note:
The Cybersecurity and Infrastructure Security Agency (CISA) is operated by the U.S. federal government with the goal of strengthening the information ecosystems of all U.S.-based organizations, regardless of sector or industry. Canada has a similar agency: the Canadian Centre for Cybersecurity. Be sure to check out the guidance provided by your own federal government’s agency(ies).
Insider Threats
When considering current and projected threats and threat trends, never lose sight of those threats or risks that can emanate from within the organization. Whether accidental or intentional, insider threats and trends must be included in your research. One prominent example is potential threats from the rise in overall employee stress levels as a result of the COVID pandemic. The impact of potential job loss, health concerns, working remotely, and social isolation caused a massive increase in anxiety. This resulted in potentially drastic changes in the behavior of employees and necessitated planning to address the risks involved.
Suggested Resources
There are many places to go to research current and projected threats and threats trends. If you’re looking for some ideas, here are a few places I would recommend:
General Sources
Some general sources for researching current and projected threats and threat trends are outlined here. Some also includes recommendations for remediation of these threats and threat trends. Be aware, you will be asked to register for most of these.
- Microsoft Digital Defense Report (MDDR): Microsoft Digital Defense Report and Security Intelligence Reports
- Crowdstrike Global Threat Report: 2022 Global Threat Report (crowdstrike.com)
- Verizon Data Breach Investigation Report (DBIR): 2021 Data Breach Investigations Report | Verizon
- FireEye Threat Intelligence Reports: Cyber Threat Intelligence Reports | FireEye
- Mandiant Threat Intelligence Directly From the Front Lines: Threat Intelligence Platform | Threat Intelligence Tools | Mandiant
- IBM Security X-Force Threat Intelligence Index: IBM Security X-Force Threat Intelligence Index | IBM
- Gartner Top Security and Risk Trends for 2022: Gartner Top Security and Risk Trends for 2022
- McKinsey Cybersecurity trends: Looking over the horizon: Cybersecurity trends: Looking over the horizon | McKinsey
- SNAS NewsBites: https://www.sans.org/newsletters/newsbites/
- Splunk Top 50 Security Threats: Top 50 Security Threats | Splunk
- MITRE ATT&CK: MITRE ATT&CK®
- MITRE D3FEND (currently in early beta): Resources | MITRE D3FEND™
- McAfee Labs Threat Report: McAfee Labs Threats Reports – Threat Research | McAfee
- Perch MSP Threat Report: 2021 MSP Cyber Threat Report | ConnectWise
- Digital Attack Map (Top Daily DDoS Attacks Worldwide): https://www.digitalattackmap.com/
Side Note:
Many of the above sources also provide more targeted data about industries and global regions as well.
Industry-Specific Sources
Some samples of industry-specific sources for researching current and projected threats and threat trends are:
- Financial Services Information Sharing and Analysis Center (FS-ISAC): Financial Services Information Sharing and Analysis Center (fsisac.com)
- FS-ISAC Annual Global Intelligence Report: Navigating Cyber 2022 (fsisac.com)
- Health Information Sharing and Analysis Center (H-ISAC): Health Information Sharing and Analysis Center | H-ISAC
- National Critical Infrastructure Resilience (Part of H-ISAC): National Critical Infrastructure Resilience – Health Information Sharing and Analysis Center | H-ISAC
National Sources
Some examples of national government sources for researching current and projected threats and threat trends are:
- U.S. Cybersecurity and Infrastructure Security Agency (CISA): Homepage | CISA
- Alerts: Alerts | CISA
- Canadian Centre for Cybersecurity: Canadian Centre for Cyber Security
- Reports and Assessments: Reports and assessments – Canadian Centre for Cyber Security
- Australian Cyber Security Centre (ACSC): https://www.cyber.gov.au/acsc/view-all-content
- United Kingdom National Cyber Security Centre: National Cyber Security Centre – NCSC.GOV.UK
- Advice and Guidance: https://www.ncsc.gov.uk/section/advice-guidance/all-topics
Putting It All Together
Once you have complied and reviewed the findings from your research (i.e., from global, region and industry-oriented sources), you will see recurring themes through the material. These common threads will arise and provide you with an understanding of what are the most likely and impactful threats and threat trends to anticipate. When you couple this with an understanding of what assets are of most value to the organization (as discussed at the top), you will then be able to prioritize and account for them in your strategic planning.
One final note: It is critical to remember that the identification of threat trends should also cover current and rapidly rising threats. While it is vital to keep an eye to the future, never forget bad actors are looking to leverage every crisis for their gain. And they are usually able to do so in depressingly rapid fashion. Always be aware of new developments and how they can affect your organization. Needless to say, this will require you to pivot and adapt your cybersecurity strategy as well.
Side Note:
The onset of the COVID pandemic was rapid and unexpected, catching organizations around the world completely off-guard. The associated rise of remote work across the globe as a result of the quarantines presented the drastic threat trend of workers being compromised from their own home networks and allowing bad actors to subsequently gain access to corporate resources. While the crisis did not allow much time for organizations to anticipate and prepare for this situation, many enterprises were able to quickly assess the risk and deploy solutions to further secure their remote employees’ access to corporate resources (e.g., Zero Trust, MFA, Patch Management, Secured VPN, DDoS Protection, etc.). Even now, two years later, this threat trend is not going to go away any time soon.
Thank you for your time. Be sure to stay tuned for the next posting in this series: Cybersecurity Strategy Step Four – What’s in It for Me? (Determining your Organization’s Priorities, Business Value Drivers and Principles).
Special thanks to Wesley Kuzma, Justin Yost and Jörg Finkeisen for their contributions to this blog post.
-
Step Two – Where Are You? (Understanding your Organization’s Current Cybersecurity State)
This blog walks cybersecurity professionals through the logical steps to create a practical and actionable cybersecurity strategy.
It’s impossible to figure out how to get to where you’re going without knowing where you’re starting from. You must have a crystal-clear understanding of your organization’s current cybersecurity capabilities; what you have and what you do not. Addressing the identified gaps in your capabilities – within the context of your organization’s priorities and objectives – is a fundamental goal of the cybersecurity strategy.
Every organization should regularly conduct a cybersecurity capability assessment to establish where it currently stands and identify any gaps that need to be addressed. The assessment should be comprehensive in nature and encompass not only the technical, but operational and tactical capabilities as well.
Side Note
While having a Configuration Management Database (CMDB) deployed for asset management is a notable attainment, what’s more important is what you are doing with it. Is it working within the context of a formally established Asset Management Program with Key Performance Indicators (KPIs)? Are there policies directing registration of assets? If so, what assets are registered? Hardware? Virtual? Software? Data? Is the CMDB integrated with the Change Management and Incident Management Systems respectively? Is there operational guidance in place for its ongoing use and management? The list goes on.
The cybersecurity capability assessment can be lengthy and involved, but its critical importance can’t be understated. Knowing where to focus your attention in maturing the organization’s information security function will be a major factor in whether you succeed or fail in making that function better.
When considering a cybersecurity assessment, here are some things to think about.
Fitting Within a Framework
While it isn’t strictly necessary to conduct a cybersecurity assessment in alignment with any existing cybersecurity framework (e.g., NIST CSF, COBIT or ISO 27001), structuring it within the context of a known framework makes the methodology and results easier to communicate and be understood by others in the field or familiar with cybersecurity. Also, the gaps and associated recommendations are framed within this structure, making the resulting remediations easier to assign and plan.
Most times, the information security function will have already settled on a particular cybersecurity framework as a frame of reference. If that’s the case, stick with it for the assessment. If the organization has not yet adopted a specific cybersecurity framework, choose the one which best fits with the organization’s operational model.
Side Note
Within the U.S. and Canada, most organizations in the public and private sectors adhere to the NIST Cybersecurity Framework. The COBIT and ISO 27001 frameworks are popular in Europe and around the globe. There are others and each all have their own pros and cons.
Assess What You Can Control
When conducting a cybersecurity assessment, be sure to understand the scope of the effort. Restrict yourself to assessing only those areas which are either under the direct control of the information security function or can be controlled or influenced through partnership with other areas of organization. Many public agencies, for example, have rigidly defined administrative boundaries and there is no point to assessing those agencies where you have no jurisdiction. Similarly, many global private organizations have separate legal operations that are self-governing. These will often have their own Information technology function.
Prior to engaging in an assessment, make sure you have worked out how extensive it will be and who from around the organization will be involved.
The Outside Perspective
Can you trust a self-assessment, or do you think it best to bring in an outside agency? That can be a tough question but, the truth of the matter is, very few organizations have an information security function with people 1) skilled in conducting thorough cybersecurity assessments or 2) with bandwidth to do them.
Two benefits of bringing in an outside agency are 1) neutrality and 2) expertise and experience. An outside agency has likely performed multiple assessments across a number of industries and can bring much needed perspective to the assessment. They may not be as familiar with your environment as you are but that is actually a good thing as they are also not as emotionally invested in it as you are. And, frankly, their job is to learn as much as they can from the organization about its information security function from the ground up. So, a blank slate is a good place to start from.
Side Note
A thorough cybersecurity assessment should entail face-to-face discoveries with relevant staff and management, possibly with technical reviews and the reviews of relevant documents, where appropriate. It is an intensely collaborative, immersive, and potentially lengthy experience. Be wary of some providers whose “assessments” consist merely of a questionnaire sent to the stakeholders which they’re asked to fill out and mail back for analysis. Other providers may conduct the assessment remotely with minimal interaction with staff and management.
Just make sure you know what you’re going to get for your money. For example, how do they conduct the assessment (e.g., what do they look at)? How interactive is it? What is/are the final product(s)? Assessments can be valuable if they’re done properly: with collaboration and partnership.
It’s All About the Roadmap
What good is an assessment without recommendations to address the gaps identified? The recommendations must be framed as actionable and reasonable activities that will provide tangible results. Optimally, the recommendations should be in the form of a structured roadmap that provides – at the very least – the following features:
- The recommended activities are clearly articulated as initiatives or projects with specific goals.
- The recommended initiatives and projects are directly linked to the gaps they are intended to address. Note: There is rarely a one-to-one alignment of recommendation to gap. Many single initiatives for example can address multiple gaps (or vice versa).
- The recommended activities are prioritized (i.e., both in terms of their direct criticality and according to the organization’s goals and objectives) and include estimated costs and duration.
- The roadmap presents a timeline wherein the component initiatives and projects are laid out in chronological order and with dependencies.
Most importantly, the roadmap must be laid out in a way that makes it realistically achievable to the organization. The recommendations must be doable, either with existing resources or through the addition of outside assistance. The idea, after all, is to be able to do something about those gaps.
Side Note
Be sure to also set up a Risk Registry to document gaps and risks that either did not make it into the roadmap (e.g., they were considered acceptable) or are discovered while executing the roadmap. These can be addressed as appropriate during a revision to the roadmap or during the next assessment and iteration of the roadmap.
The Question of Maturity
For some organizations, it’s not enough to understand where you stand and what gaps need to be addressed. For numerous reasons (e.g., budget, KPIs, policy), a few organizations will want to know how mature they are. This will typically entail a numerical score against their established cybersecurity framework.
It’s important to remember that many established frameworks are not intended to act as a maturity framework. This transforms the objective of the assessment from determining whether you are doing something to how well you are doing it. So, existing maturity models therefore must be leveraged and adapted in order to have some commonly accepted measurement criteria. Some assessment methods for example may use the Capability Maturity Model Integration (CMMI) model while others may use Program Review for Information Security Assistance (PRISMA) to determine maturity based on the NIST Cybersecurity Framework.
Side Note
When considering whether to determine your level of maturity in terms of your cybersecurity posture, remember this: just being able to adequately address all of the requirements of a cybersecurity framework (e.g., the 23 Categories of the five NIST Cybersecurity Framework functions) would indicate a very respectable level of maturity already.
My advice is to be careful when looking to understand your maturity. Be sure to set a benchmark for the desired level of maturity for the various cybersecurity framework control areas that is appropriate for your business/industry. Not every organization should strive for 5-out-of-5 for every cybersecurity framework category. Nor should it. That would be prohibitively expensive and drastically overshoot what the organization may deem “Acceptable Risk Levels”.
Using assessments to determine maturity is not perfect and, though they may try to be as objective and empirical as possible, determining the “maturity” of the organization’s information security function is not an exact science. It will entail a great deal of subjective input and should require some back-and-forth between the assessor and the client organization to ensure agreement on the results. If you’re OK with that, then you’re good to go.
One final thought: a cybersecurity assessment should never be used to cast judgement or to lay blame. No one will trust them, and you will never get honest answers or data. It should fundamentally be viewed as an objective, benign instrument intended to plant a stake in the ground saying, “Here is where we are” and look forward to the future and where you want to go.
Thank you for your time. Be sure to stay tuned for the next posting in this series: Cybersecurity Strategy Step Three – Who Goes There? (Understanding the Current and Projected Threat Landscape).
Special thanks to Justin Yost and Michael Howard for their contributions to this post.
-
Step One – Who Are You? (Understanding your Organization)
This blog is intended to walk cybersecurity professionals through the logical steps in creating a practical and actionable cybersecurity strategy.
Be absolutely clear on what your organization is about from the top on down.
I stated in my last post that the cybersecurity function doesn’t operate in a vacuum or for its own purposes. It’s a critical part of an organization, intended to protect the confidentiality, integrity and availability of that organization’s data and information. It’s dealing with threats both external and internal, some of them very specific (more on that in a later post). So, a fundamental requirement for any cybersecurity strategy is thoroughly understanding the organization within which information security is playing such a critical role.
The Mission, Goals and Objectives of the Organization
It’s not enough to know what your organization does: making cars, running a local government, providing health care services, selling insurance, etc. It’s important to understand what distinguishes your organization from all others and from where it derives and creates value. That word – value – is something I referred to in my last post and you’ll be seeing it very frequently throughout this series.
The most direct path to identifying the organization’s unique and distinguishing nature is via such definitive and forward-looking documents as the following:
- The Mission Statement – including any values stated in the mission statement
- The Charter (for some public-facing organizations)
- Recently published Strategies for the near- and long-term, including:
- Goals,
- Objectives and Key Results,
- Priorities and
- Roadmaps.
- Annual Reports
Also, it is crucial to note any recent directives stated by the Executive (e.g., the CEO, President, Governor, Premier, etc.) through interviews, conferences, memos and statements. These will provide more up to date context with regard to where the organization is heading.
Side Note
An organization in the manufacturing sector was forced to divest itself of a major division that was one of the original parts of the organization and part of its defining brand. This divestiture totally changed the direction of the company and necessitated a complete change in its long-term strategy.
However you do it, make sure you get a clear and thorough picture of what distinguishes the organization and what is important to its leadership.
The Goals and Objectives of Information Technology
Closer to home of course is determining the guiding vision for the IT function within your organization. Whether your organization has a CIO or equivalent, it is as important to get a clear understanding of what the IT function is striving to achieve as it is to understand what the organization is trying to achieve. One will logically follow the other of course and you want to make sure you are on top of both.
Similar to the above, the CIO would have published their own strategy with a vision for the road ahead. The strategy will often outline the CIO’s priority areas (e.g., in the form of pillars, or foundations, etc.) with stated goals and objectives. Additionally, some strategies will outline a roadmap or programs/projects/initiatives to realize and operationalize the strategy. These are critical for your purposes.
Side Note
One foundational area that most every IT strategy addresses is around security. But be sure to focus beyond that to the entire strategy. While information security is a vital part of the CIO’s strategy, the cybersecurity strategy should be about making sure the entirety of the CIO’s strategy will be realized securely.
Also, be aware of any directives or communications that come from the CIO or their leadership team that indicate a strategic, operational or tactical shift in the IT function’s direction.
Thank you for your time. Be sure to stay tuned for the next posting in this series: Cybersecurity Strategy Step Two – Where Are You? (Understanding your Organization’s Current Cybersecurity State).
-
Subscribe
Subscribed
Already have a WordPress.com account? Log in now.